Whether or not you’re a multi-billion greenback firm or a person utilizing e-mail for private functions, you’re not secure from one of the crucial frequent scams on-line – e-mail spoofing.
That sounds scary, proper? If we’re all liable to one thing malicious like e-mail spoofing, we have to study just a little about it to take the proper precautions to keep away from falling into its traps.
What’s E-mail Spoofing?(Definition)
E-mail spoofing is a cyber assault through which a scammer or hacker sends emails with a solid or pretend sender handle. The goal is to trick the recipients into considering that the emails are from a trusted supply and get them to open or reply to the message.
Spoofed emails are harmful and may pose a large risk to your privateness and safety. Usually, these emails are despatched so the hackers can ship malware, take over your on-line accounts, or steal funds or cash.
However the query is – how precisely does e-mail spoofing work? Let’s discover out!
How Does E-mail Spoofing Work?
E-mail spoofing may be accomplished simply with the assistance of a working SMTP (Easy Mail Switch Protocol) server and widespread e-mail platforms like Gmail or Outlook.
Since emails have three foremost components – an envelope, a message header, and a message physique, a hacker can compose an e-mail after which forge the fields inside that e-mail and put no matter they need into it. They’ll customise the data within the areas comparable to FROM, REPLY-TO, SUBJECT, and many others.
And since SMTP doesn’t present a option to authenticate addresses, the e-mail program reads what’s within the fields and generates what the recipient sees. So when the recipient will get the e-mail, it seems to return from a solid handle.
For instance, an attacker or hacker may create an e-mail that appears like it’s despatched from PayPal. It would include a message asking recipients to click on a hyperlink to authenticate or change their account password. This may trick the recipient into giving their credentials and account particulars, ensuing of their cash being stolen.
Causes for E-mail Spoofing
The explanations for e-mail spoofing are simple and primarily meant for legal functions. A few of the commonest causes behind this malicious act embody the next:
1. Identification Theft or Hiding Identification
One of many foremost causes behind e-mail spoofing is to cover or conceal identification. It permits the attackers or hackers to stay nameless or faux to be another person to earn their targets’ belief after which collect confidential data from them.
2. Avoiding a Spam Blacklist
A majority of e-mail suppliers let its person create a blacklist that helps them filter out spam. Therefore hackers spoof their e-mail addresses to slide previous the filters undetected and keep away from being included within the spam blacklist.
3. Tarnishing the Status of the Sender
Normally, a spoofed e-mail accommodates false data and malicious hyperlinks which might be meant to hurt the recipient not directly or the opposite. Attackers generally use this technique to ship malware through emails to tarnish the picture or status of organizations or individuals.
4. Aspiring to do Private Injury
E-mail spoofing can be utilized to realize the goal’s private data, enterprise contacts, social media accounts, and extra. Entry to this could enable the attacker to interrupt the goal’s digital life and trigger hurt or harm to their private life.
The risks of e-mail spoofing are past your management when you fall into its lure, and it’s typically fairly simple to be trapped by it. It exploits the human issue that nobody double-checks the emails they obtain.
This brings us to the subsequent query – how precisely do hackers spoof your e-mail handle? Let’s discover out within the subsequent part!
How Do Hackers Spoof E-mail Addresses?
E-mail spoofing is principally accomplished by forging the e-mail syntax, however it varies relying on which a part of the e-mail the hacker tries to forge. Listed below are 3 totally different ways in which attackers spoof emails:
1. E-mail Spoofing through Show Identify
Spoofing through show title is a kind of e-mail spoofing through which the show title of the e-mail sender is solid. This may be simply accomplished by merely registering a brand new e-mail account with the identical title because the particular person being impersonated.
So should you ever obtain an e-mail from a star asking for cash or entry to your financial institution particulars, then you definitely may be certain it’s spoofing through show title. Such a e-mail spoofing typically will get previous the safety measures because it gained’t get filtered as spam and is kind of efficient as e-mail apps don’t present metadata on smartphones.
2. E-mail Spoofing through Reputable Domains
Within the case of e-mail spoofing through professional domains, the attacker might use a trusted e-mail handle within the FROM header. This implies the show title and the e-mail handle will present the fallacious data.
For such a spoofing, the attacker doesn’t must hack into the goal’s inner community; they solely want to make use of SMTP servers that enable connections with out authentication which lets them manually specify the “To” and “From” addresses. That is very harmful as many firm e-mail domains don’t use any countermeasures for verification.
3. E-mail Spoofing through Lookalike Domains
Spoofing through lookalike domains is an e-mail spoofing through which the hacker registers and makes use of a website much like the impersonated area. The change is usually minimal, and a receiver won’t discover the distinction.
For instance, one thing like @gma1l.com as a substitute of @gmail.com. Hackers normally do that when a website is protected, and spoofing isn’t doable. With this technique, the emails bypass spam checks resulting from being professional mailboxes.
Now that you understand how hackers can spoof e-mail addresses, you’ll want to study to guard your self from them. Let’s learn the way within the subsequent part!
How you can Shield from E-mail Spoofing?
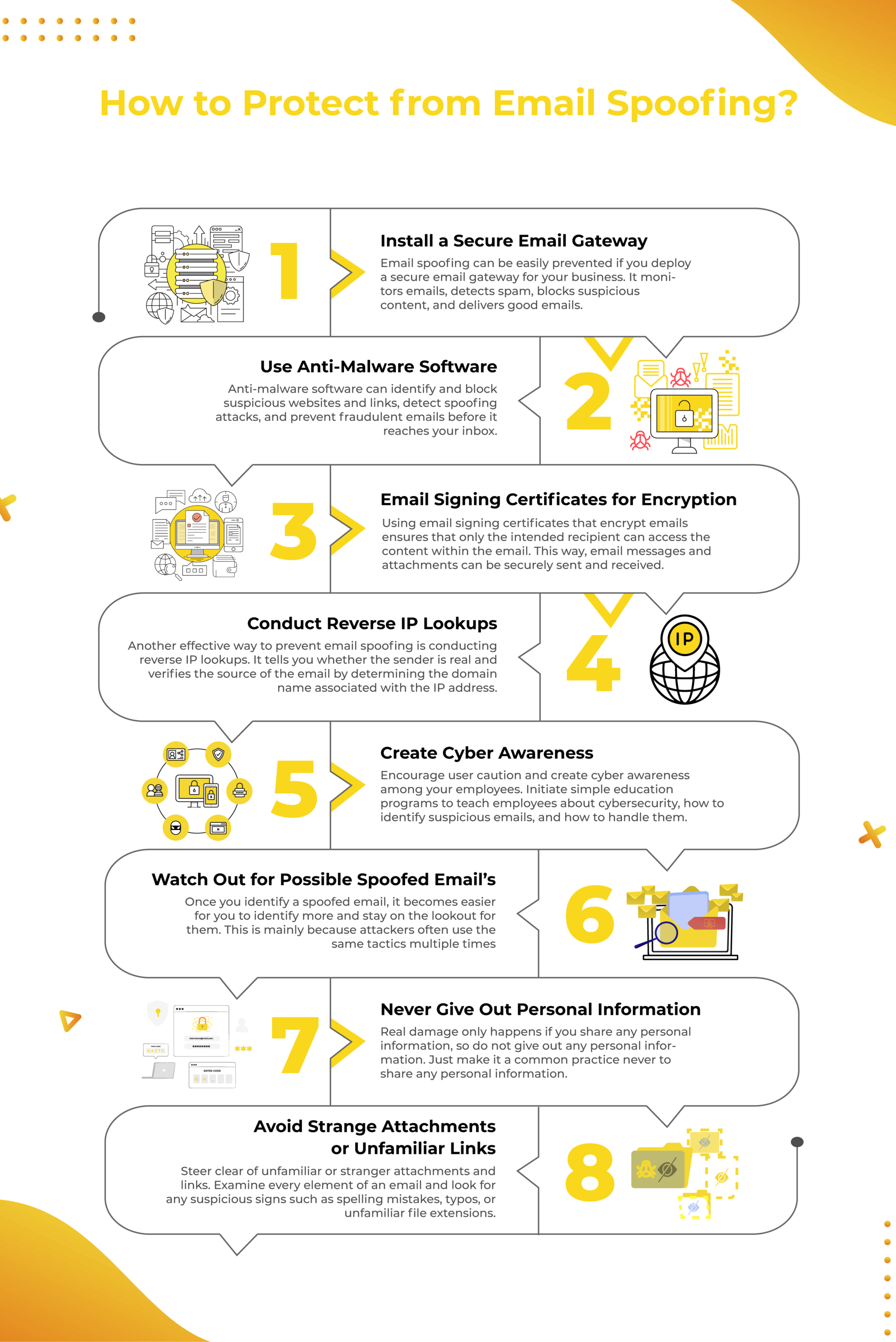
1. Set up a Safe E-mail Gateway
E-mail spoofing may be simply prevented should you deploy a safe e-mail gateway for your small business. A Safe E-mail Gateway (SEG) is software program that screens emails despatched and acquired. It detects most malware, spam, and phishing assaults.
An e-mail gateway ensures that your e-mail is safe by blocking inbound and outbound emails with suspicious components or not assembly the safety insurance policies {that a} enterprise places in place. The e-mail gateway safety prevents undesirable emails and solely delivers the nice ones.
2. Use Anti-Malware Software program

One other software program that may assist you with stopping e-mail spoofing is anti-malware software program. These software program applications can determine and block suspicious web sites and hyperlinks, detect spoofing assaults, and forestall fraudulent emails earlier than it reaches your inbox. Anti-malware software program may also work like a power subject that protects your system from spoofed emails.
3. Use E-mail Signing Certificates for Encryption
One widespread option to forestall e-mail spoofing is by utilizing e-mail signing certificates that encrypt emails. Solely the meant recipient can entry the content material inside the e-mail.
E-mail encryption certificates use uneven encryption, the place a public key encrypts the e-mail and sends it to the recipient. The recipient then will get a non-public key to assist them decrypt the message. This fashion, e-mail messages and attachments may be securely despatched and acquired.
Furthermore, to make sure your recipients that the supply of the e-mail and its contents are legitimate and genuine, you can too add your digital signature to it.
4. Conduct Reverse IP Lookups
A easy but efficient option to determine e-mail spoofing is by conducting reverse IP lookups. It tells you whether or not the sender is actual, verifies the e-mail’s supply by figuring out the area title related to the IP handle, and even tells you the place the e-mail got here from.
You should use on-line reverse lookup instruments to find out the area title related to the IP handle. On this case, if the IP handle differs from the place the e-mail was supposed to return from, you possibly can simply determine the e-mail spoofing assault. This makes it an e-mail spoofing check.
You too can publish a Area Identify System (DNS) file that states who can ship emails on behalf of your area in order that the messages may be inspected earlier than downloading. This can assist you block or reject content material earlier than it causes any hurt.
5. Create Cyber Consciousness
You’ll be able to depend on expertise and new software program to fight e-mail spoofing. Nonetheless, it turns into way more efficient should you encourage person warning and create cyber consciousness amongst your staff.
In case your staff are unaware, a pretend e-mail may look actual. So, you’ll want to provoke easy teaching programs to show staff about cybersecurity, easy methods to determine suspicious emails, and easy methods to deal with them.
Whereas coaching your staff about cyber consciousness, it’s essential to periodically replace the coaching supplies and instructing strategies to maintain up with the brand new developments within the e-mail spoofing space.
6. Watch Out for Attainable Spoofed E-mail Addresses
As a rule, the form of e-mail addresses that you just see in messages are acquainted or predictable, so you possibly can study to be careful for unknown or suspicious e-mail addresses. In case you get a wierd e-mail, you possibly can confirm its origin earlier than interacting with the content material.
When you determine a spoofed e-mail, it turns into simpler so that you can determine extra and keep looking out for them. That is primarily as a result of attackers typically use the identical ways a number of occasions. So all the time keep vigilant!
7. By no means Give Out Private Data
This one is a no brainer – by no means give out private or confidential data. Typically, even when a spoofed e-mail makes it into your inbox, actual harm solely occurs should you share any private data. So the only factor you are able to do isn’t give out private data. Make it a standard apply by no means to share private data, and voila, you may be considerably limiting the harm of an e-mail spoofing assault.
8. Keep away from Unusual Attachments or Unfamiliar Hyperlinks
Right here’s one other no-brainer – keep away from unfamiliar or stranger attachments and hyperlinks. You are able to do this by analyzing each ingredient of an e-mail and in search of any suspicious indicators, comparable to spelling errors, typos, or unfamiliar file extensions. You too can attempt to discover out the supply of a hyperlink by right-clicking or lengthy tapping it.
Wrap Up
There’s no denying that e-mail spoofing assaults will occur sooner or later. So it’s as much as us to take the proper measures to forestall or determine it earlier than it causes any actual harm.
By following these easy strategies, you possibly can make sure that your inbox is secure from the malicious intentions of attackers. We hope that we’ve got helped you study just a little about e-mail spoofing and easy methods to sort out it. Keep secure, of us! Completely satisfied emailing!
Additional Reads
VPN: How Does it Work & How you can Select the Proper One?
9 Greatest E-mail Cleaners in 2023 (Paid & Free)
9 Greatest Spying Instruments to Hold Eye on Rivals!
11 E-mail Verification Instruments to Test Out in 2023
21 Gmail Plugins for Good Professionals!
The 11 Greatest E-mail Monitoring Instruments & Software program!