by Sundance
Throughout my journey to DC in the summertime of 2020 there have been a myriad of disconcerting datapoints assembled; revelations that made sense of the insanity and disappointments discovered in all places. Nonetheless, one of many key notations for future reference was to observe the political evolution of Dept of Homeland Safety (DHS) and spot the leap the place the ideological outlook turns into particular authorities motion.
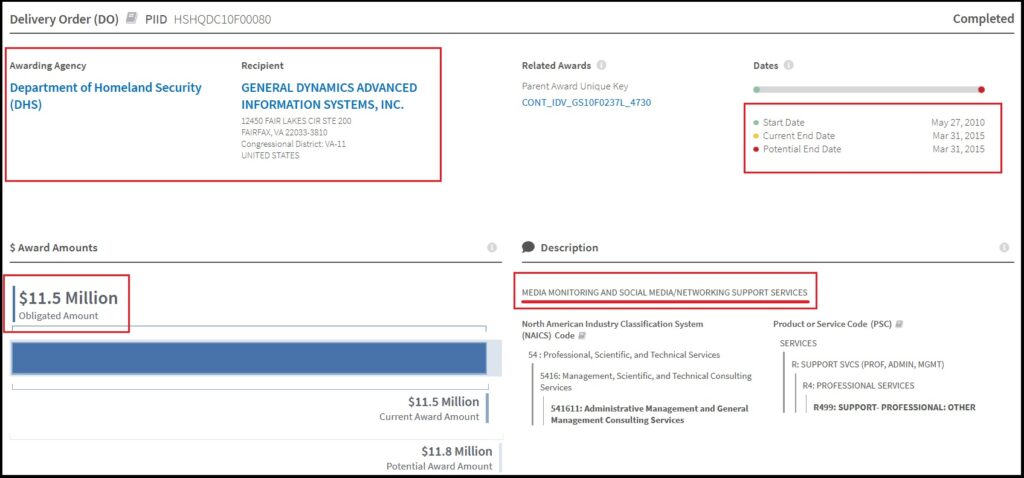
With that in thoughts, this latest discovery of a 2010 to 2015 DHS contract to a really well-known USG protection contractor, Basic Dynamics Superior Info Methods Inc., surfaces.
As many are actually changing into conscious, DHS is the lead company behind the entire engagements with Twitter and different social media.
The Workplace of the Director of Nationwide Intelligence (ODNI), particularly created as an end result of the post-911 Patriot Act, is the pivot level on the surveillance radar sweep.
Previous to the DNI the final Intelligence Group (IC) surveillance confronted offshore and swept international adversaries. If any menace was picked up that included the potential for home terrorism, the recognized contact transferred from the CIA, NSA, DoD into the DOJ and FBI. The DOJ then used the FISA Court docket to request switch of concentrating on from international to home.
Nonetheless, after 911 it was decided the nationwide safety surveillance radar wanted to comb a full 360° to incorporate home surveillance. The ODNI was the workplace created to handle the pivot level. As a selected end result of the Patriot Act, Americans had been now beneath the identical surveillance as international adversaries. The brand new definition of Americans being threats to the nationwide safety state is in the end what led to our taking off sneakers at TSA checkpoints in airports. TSA is a subsidiary company of DHS.
Offshore surveillance now flowed from the CIA, DoD, NSA, IC into the ODNI, who then filtered it, and if wanted transferred it to the newly created DHS.
Because the design was laid out, the DHS would then contact the DOJ or FBI whereas affording the U.S. particular person (goal) in query their duly constitutional protections towards illegal searches and seizures. The sketchy authorized dynamic is what created the necessity for the DOJ Nationwide Safety Division (DOJ-NSD).
On the identical time, onshore home surveillance could be carried out by DHS by way of new techniques just like the Transportation Security Administration and so on. Native, state and federal regulation enforcement would determine points or investigative targets, then ship the concentrating on knowledge upstream into the DHS database. DHS transfers the discovering to the ODNI who cross-reference it with CIA, NSA, and so on. This was the unique design.
Nonetheless, it was particularly Barack Obama and Eric Holder who noticed a possibility with the newly created system. The outcome, DHS home surveillance was weaponized. The timing of this DHS contract (2010) to Basic Dynamics for “media monitoring and social media help” matches completely in step with the recognized timeline of how DHS was weaponized.

Barack Obama and Eric Holder didn’t create a weaponized DOJ and FBI; the establishments had been already weaponized by the Patriot Act. What Obama and Holder did was take the preexisting system and retool it, so the weapons of presidency solely focused one aspect of the political continuum.
This level is the place many individuals understandably get confused.
Elevator Speech:
(1) The Patriot Act turned the intel surveillance radar from international searches for terrorists to home searches for terrorists.
(2) Obama/Biden then redefined what’s a “terrorist” to incorporate their political opposition.
DEEP DIVE:
Twitter is to the U.S. authorities as TikTok is to China. The overarching dynamic is the necessity to management public perceptions and opinions.
DHS has been in ever growing management of Twitter for the reason that public-private partnership was shaped in 2011/2012. Nonetheless, it’s not simply Twitter. The identical elementary relationships are actually at work inside Google, Microsoft, YouTube, Instagram and Fb.
With all of the shiny issues surfacing from the Twitter Recordsdata, few are wanting on the origin of what the federal government is attempting to maintain hidden….
 Within the period shortly after 9/11 the DC nationwide safety equipment, instructed by Vice President Dick Cheney, was constructed to protect continuity of presidency and concurrently view all People as potential threats. The Division of Homeland Safety (DHS) and the Workplace of the Director of Nationwide Intelligence (ODNI) had been created particularly for this goal.
Within the period shortly after 9/11 the DC nationwide safety equipment, instructed by Vice President Dick Cheney, was constructed to protect continuity of presidency and concurrently view all People as potential threats. The Division of Homeland Safety (DHS) and the Workplace of the Director of Nationwide Intelligence (ODNI) had been created particularly for this goal.
After 9/11/01 the digital surveillance system that was initially created to observe threats from overseas was retooled to observe threats inside our nation. That’s when all of our digital ‘metadata’ got here beneath federal surveillance.
That inflection level, and the method that adopted, was precisely what Edward Snowden tried to level out.
What Barack Obama and Eric Holder did with that new assemble was refine the inner concentrating on mechanisms in order that solely their political opposition turned the goal of this new nationwide safety system.
The issues we face now as a rustic are instantly an end result of two very distinct factors that had been merged by Barack Obama. (1) The put up 9/11 monitoring of digital communication of Americans; and (2) Obama’s group making a fine-tuning knob that it targeted on the politics of the targets. This is essential to grasp as you dig deeper into this analysis define.
Washington DC created the fashionable nationwide safety equipment instantly and hurriedly after 9/11/01. The Division of Homeland Safety got here alongside in 2002, and inside the Intelligence Reform and Terrorism Prevention Act of 2004 the Workplace of the Director of Nationwide Intelligence (ODNI) was shaped.
When President Barack Obama and Legal professional Basic Eric Holder arrived just a few years later, these newly shaped establishments had been seen as alternatives to create a really particular nationwide safety equipment that might focus virtually solely towards their political opposition.
The preexisting Federal Bureau of Investigation (FBI) and Dept of Justice (DOJ) had been then repurposed to develop into two of the 4 pillars of the home nationwide safety equipment: a home surveillance state. Nonetheless, this new assemble would have a concentrating on mechanism primarily based on political ideology.
The DHS, ODNI, DOJ and FBI turned the 4 pillars of this new establishment. Atop these pillars is the place you will see that the Fourth Department of Authorities.
We weren’t sleeping when this occurred, we had been conscious. Nonetheless, we had been stunningly distracted by the financial collapse that was happening in 2006 and 2007 when the engineers behind Obama began to assemble the design. By the point Obama took workplace in 2009, we sensed one thing profound was shifting, however we will solely see precisely what shifted within the aftermath. The 4 pillars had been put into place, and a brand new Fourth Department of Authorities was quietly created.
As time handed, and the system operators turned aware of their new instruments, know-how allowed the tentacles of the system to achieve out and contact us. That’s after we first began to note that one thing very disconcerting was occurring. These 4 pillars are the basis of it, and if we take the time to grasp how the Fourth Department originated, questions on this present state of perpetual angst will begin to make sense.
We decide up the expansive and weaponized intelligence system because it manifests after 9/11/01, and my objective is to spotlight how the fashionable model of the overall intelligence equipment has metastasized right into a Fourth Department of Authorities. It’s this superseding department that now touches and influences each aspect of our life. We The Folks are beneath surveillance.
If we take the fashionable assemble, originating on the pace of technological change, we will additionally see how the oversight or “examine/stability” in our system of presidency turned functionally obsolescent.
After a few years of granular analysis concerning the intelligence equipment inside our authorities, in the summertime of 2020 I visited Washington DC to ask particular questions. My objective was to go the place the affect brokers inside authorities truly function, and to find the individuals deep contained in the establishments nobody elected, and few individuals take note of.

It was throughout this course of once I found how data is purposefully put into containment silos; basically a proper course of to dam the move of knowledge between companies and between the unique branches. Whereas irritating to find, the silo impact was necessary as a result of understanding the communication between networks results in our skill to reconcile battle between what we understand and what’s truly happening.
After days of analysis and conferences in DC throughout 2020; amid a city that was serendipitously shut down resulting from COVID-19; I discovered a letter slid beneath the door of my room in an almost empty resort with an introduction of types. The next discussions had been maybe an important. After many hours of particular questions and solutions on particular examples, I noticed why our nation is on this mess. That’s once I found the fourth and superseding department of presidency, the Intelligence Department.
I’m going to elucidate how the Intelligence Department works: (1) to manage each different department of presidency; (2) the way it features as a completely impartial department of presidency with no oversight; (3) how and why it was created to be impartial from oversight; (4) what’s the present mission of the IC Department, and most significantly (5) who operates it.
The Intelligence Department is an impartial functioning department of presidency, it’s not a subsidiary set of companies inside the Government Department as most would suppose. To grasp the Intelligence Department, we have to drop the elementary college civics class classes about three coequal branches of presidency and change that outlook with the fashionable system that created itself.
The Intelligence Department features very similar to the State Dept, by way of a singular set of public-private partnerships that help it. Large Tech business collaboration with intelligence operatives is a part of that functioning, virtually like an NGO. Nonetheless, the method is far more necessary than most suppose. On this problematic perspective of a corrupt system of presidency, the method is the flaw – not the result.
There are individuals making choices inside this little recognized, unregulated and out-of-control department of presidency that affect each aspect of our lives.
Not one of the individuals working deep contained in the Intelligence Department had been elected; and our elected consultant Home members genuinely have no idea how the system works. I assert this place affirmatively as a result of I’ve talked to Home and Senate staffers, together with the chiefs of employees for a number of Home & Senate committee seats. They don’t seem to be malicious individuals; nevertheless, they’re genuinely clueless of issues that occur outdoors their silo. That’s a part of the aim of me explaining it, with examples, in full element with daylight.
We start….
In April of 2016, the FBI launched a counterintelligence operation towards presidential candidate Donald Trump. The questioning about that operation is what New York Consultant Elise Stefanik cites in March of 2017, roughly 11 months later (First Two Minutes).
Issues to notice:
♦ Discover how FBI Director James Comey simply matter-of-factly explains nobody outdoors the DOJ was knowledgeable concerning the FBI operation. Why? As a result of that’s simply the way in which issues are achieved. His justification for unilateral operations was “due to the sensitivity of the matter“, completely ignoring any constitutional or regulatory framework for oversight; as a result of, effectively, fairly merely, there isn’t any. The intelligence equipment contained in the DOJ/FBI can, and does, function primarily based on their very own impartial determinations of authority.
♦ Discover additionally how FBI Director Comey shares his perspective that informing the Nationwide Safety Council (NSC) is the equal of notifying the White Home. The FBI management expressly consider they bear no accountability to temporary the Chief Government. So long as they inform some unknown, unelected, bureaucratic entity contained in the NSC, their unwritten accountability to tell the highest of their institutional silo is full. If the IC needs to carve out the Oval Workplace, they merely plant data contained in the NSC and, from their perspective, their civic accountability to comply with checks-and-balances is full. That is an intentional assemble.
♦ Discover how Comey obfuscates notification to the Director of Nationwide Intelligence (DNI), by avoiding the very fact James Clapper was the DNI from outset of the counterintelligence operation all through the rest of Obama’s time period. After I get deeper into the method, we are going to perceive how the Intelligence Department has deliberately used the creation of the DNI place (established put up 9/11/01) as a way to keep away from oversight, not improve it. Holding an oblivious doofus like James Clapper in place held strategic worth [Doofus Reminder HERE].
That video of James Comey being questioned by Elise Stefanik was the primary instance given to me by somebody who knew the background of the whole lot that was happening previous that March 20, 2017, listening to. That FBI reference level is a key to grasp how the Intelligence Department operates with unilateral authority above Congress (legislative department), above the White Home (government department), and even above the courtroom system (judicial department).
Additionally, watch this brief video of James Clapper, as a result of it’s probably many readers have forgotten, and sure much more readers have by no means seen it. Watch intently how then White Home nationwide safety adviser John Brennan is responding in that video. That is earlier than Brennan turned CIA Director, that is when Brennan was serving to Barack Obama put the pillars into place. WATCH:
[Sidebar: Every time I post this video it gets scrubbed from YouTube (example), so save it if you ever want to see it again.]
The video of James Clapper highlights how the ODNI place (created with good nationwide safety intention) ended up changing into the fulcrum for contemporary weaponization, and is now an workplace manipulated by companies with a vested curiosity in retaining energy. The Intelligence Department holds energy over the ODNI by way of their affect and partnership with the physique that authorizes the ability inside it, the Senate Choose Committee on Intelligence (SSCI).
Factually, the fashionable intelligence equipment makes use of checks and balances of their favor. The checks create silos of proprietary data, labeled data, vaults of knowledge that work round oversight points. The silos, which embrace the exploitation of the International Intelligence Surveillance Court docket (FISA Court docket, or FISC) are a part of the issue.
Sarcastically, the Workplace of the Director of Nationwide Intelligence was created within the aftermath of 9/11/01 expressly to remove the silos of knowledge which they felt led to a home terrorist assault that would have been prevented. The ODNI was created particularly upon the advice of the 9/11 fee.
The intent was to create a central hub of intelligence data, contained in the Government Department, the place the CIA, NSA, DoD, DoS, and DIA may deposit their distinctive intelligence merchandise and a repository could be created in order that home intelligence operations, just like the DOJ and FBI may entry them when wanted to investigate threats to the U.S. This, they hoped, would guarantee the apparent flags missed within the 9/11 assaults wouldn’t be missed once more.
Nonetheless, the creation of the DNI workplace additionally created an unconstitutional surveillance system of the American individuals. The DNI workplace turned the device to take huge quantities of knowledge and use it to focus on particular People. Weaponizing the DNI workplace for political concentrating on is now the aim of the DNI workplace because it exists.
The unlawful and illegal nature of the surveillance creates a necessity for cautious safety amid the group who function within the shadows of digital data and home surveillance. You will notice the way it was vital to put in an individual uniquely expert in being an fool, James Clapper, into that willfully blind position whereas intelligence operatives labored across the workplace to assemble the Intelligence Department of Authorities.
• The final federal price range that flowed by way of the standard budgetary course of was signed into regulation in September of 2007 for fiscal yr 2008 by George W. Bush. Each price range since then has been a fragmented course of of constant resolutions and particular person spending payments.
Why does this matter? As a result of many individuals suppose defunding the Intelligence Group is an answer; it isn’t…. not less than, not but. Worse but, the corrupt divisions deep contained in the U.S. intelligence system can now fund themselves from multinational personal sector partnerships (banks, firms and international entities).
• When Democrats took over the Home of Representatives in January 2007, they took workplace with a plan. Nancy Pelosi turned Speaker, and Democrats managed the Senate the place Harry Reid was Majority Chief. Barack Obama was a junior senator from Illinois.
Pelosi and Reid deliberately didn’t advance a price range in 2008 (for fiscal yr 2009) as a result of their plan included putting in Barack Obama (and all that got here with him) with an open checkbook made much more profitable by a worsening monetary disaster and a course of known as baseline budgeting. Baseline budgeting means the prior fiscal yr price range is accepted as the start line for the subsequent yr price range. All earlier expenditures are baked into the cake inside baseline budgeting.
Huge bailouts preceded Obama’s set up resulting from U.S. financial collapse, and large bailouts continued after his set up. That is the ‘by no means let a disaster go to waste’ facet. TARP (Troubled Asset Restoration Program), auto bailouts (GM), and the large stimulus spending invoice, the American Restoration and Reinvestment Act (ARRA, ie. these shovel prepared jobs) had been all a part of the non-budget spending. The federal reserve assisted with Quantitative Easing (QE1 and QE2) as congress handed numerous Porkulous spending payments additional spending and changing the formal price range course of.
Word: There has by no means been a price range handed within the regular/conventional course of since September of 2007.
• Whereas Obama’s radical ‘transformation‘ was triggered throughout a broad vary of presidency establishments, concurrently spending on the U.S. army was lower, however spending on the intelligence equipment expanded. We had been all distracted by Obamacare, and the Republican Get together needed to maintain us that method. Nonetheless, within the background there was a strategy of transformation happening that included very particular motion by Eric Holder and focused effort towards the most recent government company the ODNI.
 The individuals behind Obama, those self same individuals now behind Joe Biden, knew from years of strategic planning that ‘radical transformation’ would require management over particular parts contained in the U.S. authorities. Eric Holder performed a key position in his place as U.S. Legal professional Basic within the DOJ.
The individuals behind Obama, those self same individuals now behind Joe Biden, knew from years of strategic planning that ‘radical transformation’ would require management over particular parts contained in the U.S. authorities. Eric Holder performed a key position in his place as U.S. Legal professional Basic within the DOJ.
AG Holder recruited ideologically aligned political operatives who had been conscious of the bigger institutional goals. A type of goals was weaponizing the DOJ-Nationwide Safety Division (DOJ-NSD) a division contained in the DOJ that had no inspector common oversight. For most individuals the DOJ-NSD weaponization surfaced with a hindsight awakening of the DOJ-NSD concentrating on candidate Donald Trump a few years later. Nonetheless, by then the Holder crew had executed virtually eight full years of background work.
• The second bigger Obama/Holder goal was management over the FBI. Why was that necessary? As a result of the FBI does the home investigative work on anybody who wants or holds a safety clearance. The removing of safety clearances could possibly be used as a filter to additional construct the inner ideological military they had been assembling. Moreover, with new energy within the ODNI created as a downstream consequence of the Patriot Act, new protocols for U.S. safety clearances had been simple to justify.
Fastidiously choosing fellow ideological vacationers was facilitated by this filtration inside the safety clearance course of. How does that difficulty later manifest? Simply go searching at how politicized each intelligence company has develop into, particularly together with the FBI.
• At the very same time this new background safety clearance course of was ongoing, once more everybody distracted by the battle over Obamacare, contained in the Division of State (Secretary Hillary Clinton) a political alignment making room for the subsequent part was being assembled. Names like Samantha Energy, Susan Rice and Hillary Clinton had been acquainted on tv whereas Lisa Monaco labored as a authorized liaison between the Obama White Home and Clinton State Division.
By means of the Dept of State (DoS) the intelligence equipment started engaged on their first steps to align Large Tech with a bigger home institutional goal. These of you who keep in mind the “Arab Spring”, some say “Islamist Spring”, will keep in mind it was triggered by Barack Obama’s speech in Cairo – his first international journey. The State Division labored with grassroots organizers (principally Muslim Brotherhood) in Egypt, Syria, Bahrain, Qatar and Libya. Obama leaned closely on the organizational community of Turkish President Recep Erdogan for contacts and help.
Why does this facet matter to us? Properly, you would possibly keep in mind how a lot effort the Obama administration put into recruiting Fb and Twitter as sources for the assorted mideast rebellions the White Home and DoS supported. This was the purpose of contemporary merge between the U.S. intelligence group and Large Tech social media.
In some ways, the coordinated political outcomes in Libya and Egypt had been the beta take a look at for the coordinated home political outcomes we noticed within the 2020 U.S. presidential election. The U.S. intelligence group working with social media platforms and political operatives.
Overlaying all of that background exercise was additionally a brand new alignment of the Obama-era intelligence equipment with ideological federal “contractors“. The place does this contractor exercise manifest? Within the FISA Court docket opinion of Rosemary Collyer who cited the “interagency memorandum of understanding”, or MOU.
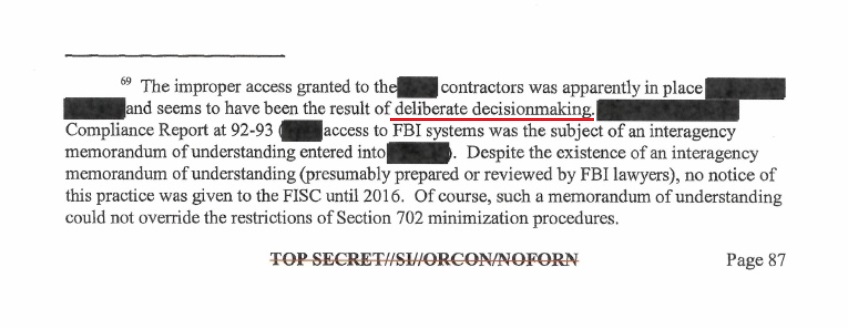
Hopefully, you’ll be able to see a small a part of how tentacled the system to arrange/weaponize the intelligence equipment was. None of this was unintentional, all of this was by design, and the USA Senate was liable for deliberately permitting most of this to happen. The instruments the federal government used to observe threats had been now getting used to observe each American. WE THE PEOPLE had been now the menace the nationwide safety system was monitoring.
That’s the 30,000/ft degree backdrop historical past of what was occurring as the fashionable IC was created. Subsequent, we are going to go into how all these numerous intelligence networks started working in unison and the way they presently management the entire different DC establishments beneath them; together with how they’ll carve out the President from understanding their exercise.
♦ When Barack Obama was put in in January 2009, the Democrats held a 60-seat majority within the U.S. Senate. Because the individuals behind the Obama set up started executing their longer-term plan, the Senate Choose Committee on Intelligence was a device to create the Intelligence Department; it was not an unintentional sequence of occasions.
When Obama was put in, Dianne Feinstein was the Chair of the Senate Choose Committee on Intelligence (SSCI), and Democrat operative Dan Jones was her lead staffer. Feinstein was utterly managed by these round her together with Senate Majority Chief Harry Reid. The CIA was within the strategy of turning over personnel following the Bush period, and on account of a large multi-year narrative of diminished credibility (Iraq WMD), a deep purge was underway. Obama/Holder had been within the strategy of shifting intelligence alignment and the intensely political Democrat Chief Harry Reid was a key participant.
 THE TRAP – Many individuals say that Congress is the answer to eliminating the Fourth and superseding Department of Authorities, the Intelligence Department. That is an train in futility as a result of the Legislative Department, particularly the SSCI, facilitated the creation of the Intelligence Department. The SSCI can not put the genie they created again within the bottle with out admitting they too are corrupt; and the background story of their corruption is method too intense to be uncovered now.
THE TRAP – Many individuals say that Congress is the answer to eliminating the Fourth and superseding Department of Authorities, the Intelligence Department. That is an train in futility as a result of the Legislative Department, particularly the SSCI, facilitated the creation of the Intelligence Department. The SSCI can not put the genie they created again within the bottle with out admitting they too are corrupt; and the background story of their corruption is method too intense to be uncovered now.
Each member of the SSCI is compromised in some controlling method. These Senators who disliked the management over them; particularly disliked as a result of the chance of daylight was tenuous and, effectively, doable; have both left utterly or stepped down from the committee. Not one of the SSCI members previous or current would ever ponder saying brazenly what their tenure concerned.
[Note: You might remember when Vice Chairman Mark Warner’s text messages surfaced, there was a controlled Republican SSCI member who came to his defense in February of 2018. It was not accidental that exact Senator later became the chair of the SSCI himself. That Republican Senator is Marco Rubio, now vice-chair since the Senate re-flipped back to the optics of Democrat control in 2021.]
All of President Obama’s 2009 intelligence appointments required affirmation from the Senate. The nominees needed to first move by way of the Democrat managed SSCI, after which to a full Senate vote the place Democrats held a 60-vote majority. Primarily, Obama acquired everybody he needed in place simply. Rahm Emmanuel was Obama’s Chief of Workers, and Valerie Jarrett was Senior Advisor.
 Tim Geithner was Treasury Secretary in 2010 when the joint DOJ/FBI and IRS operation to focus on the Tea Get together came about after the midterm “shellacking” brought on by the Obamacare backlash. Mitch McConnell was Minority Chief within the Senate however supported the concentrating on of the Tea Get together as his Senate colleagues had been getting primaried by an indignant and efficient grassroots marketing campaign. McConnell’s pal, Senator Bob Bennett, getting overwhelmed in Utah was the ultimate straw.
Tim Geithner was Treasury Secretary in 2010 when the joint DOJ/FBI and IRS operation to focus on the Tea Get together came about after the midterm “shellacking” brought on by the Obamacare backlash. Mitch McConnell was Minority Chief within the Senate however supported the concentrating on of the Tea Get together as his Senate colleagues had been getting primaried by an indignant and efficient grassroots marketing campaign. McConnell’s pal, Senator Bob Bennett, getting overwhelmed in Utah was the ultimate straw.
Soiled Harry and Mitch McConnell noticed the TEA Get together by way of the identical prism. The TEA Get together took Kennedy’s seat in Massachusetts (Scott Brown); Sharon Angle was about to take out Harry Reid in Nevada; Arlen Spector was taken down in Pennsylvania; Senator Robert Byrd died; Senator Lisa Murkowski misplaced her main to Joe Miller in Alaska; McConnell’s nominee Mike Citadel misplaced to Christine O’Donnell in Delaware; Rand Paul gained in Kentucky. That is the background. The peasants had been revolting…. and visibly indignant Mitch McConnell desperately made a cope with the satan to guard himself.
In some ways, the TEA Get together motion was/is similar to the MAGA motion. The distinction in 2010 was the absence of a head of the motion, in 2015 Donald Trump turned that head determine who benefited from the TEA Get together power. Trump got here into workplace in 2017 with the identical congressional opposition because the profitable TEA Get together candidates in 2011.
Republicans took management of the Senate following the 2014 mid-terms. Republicans took management of the SSCI in January 2015. Senator Richard Burr turned chairman of the SSCI, and Dianne Feinstein shifted to Vice-Chair. Soiled Harry Reid left the Senate, and Mitch McConnell took energy once more.
Republicans had been in charge of the Senate Intelligence Committee in 2015 when the Intelligence Department operation towards candidate Donald Trump was underway. [Feinstein’s staffer, Dan Jones, left the SSCI so he could act as a liaison and political operative between private-sector efforts (Fusion GPS, Chris Steele) and the SSCI.] The SSCI was a participant in that Fusion GPS/Chris Steele operation, and as a direct consequence Republicans had been inherently tied to the issue with President Trump taking workplace in January of 2017. Indiana Republican Senator Dan Coats was a member of the SSCI.
Backside line…. When it got here to the intelligence system concentrating on Donald Trump in the course of the 2015/2016 main, the GOP was simply as a lot in danger as their Democrat counterparts.
When Trump unexpectedly gained the 2016 election, the SSCI was shocked greater than most. They knew countermeasures would must be deployed to guard themselves from any publicity of their prior intelligence conduct. Instantly Senator Dianne Feinstein stepped down from the SSCI, and Senator Mark Warner was elevated to Vice Chairman.
Indiana’s personal Mike Pence, now Vice President, really useful fellow Hoosier, SSCI Senator Dan Coats, to develop into President Trump’s Director of Nationwide Intelligence (ODNI). [Apply hindsight here]
• To offer an thought of the Intelligence Department energy dynamic, remind your self how Home Everlasting Choose Committee on Intelligence (HPSCI), Chairman Devin Nunes, tried to get entry to the DOJ/FBI data of the FISA software used towards the Trump marketing campaign by way of Carter Web page.
Bear in mind, Devin Nunes solely noticed a portion of the FISA path from his overview of a Presidential Each day Transient (PDB) beforehand given to President Obama. Chairman Nunes needed to overview the PDB on the White Home SCIF resulting from compartmented intelligence, one other instance of the silo profit.
Bear in mind the large stonewalling and blocking of the DOJ/FBI towards Nunes? Bear in mind the back-and-forth battle over declassification surrounding the Nunes memo?
Bear in mind, after Nunes went on to Home Speaker Paul Ryan for assist (didn’t get any), the DOJ solely permitted two members from every celebration inside the HPSCI to overview the paperwork, and solely on the DOJ workplaces of fundamental justice?
Distinction that quantity of Home Intel Committee railroading by intelligence operatives within the DOJ, DOJ-NSD and FBI, with the easy request by Senate Intelligence Vice Chairman Mark Warner asking to see the Carter Web page FISA software and instantly a duplicate being delivered to him on March seventeenth 2017.
Are you able to see which intelligence committee is aligned with the deepest a part of the deep state?
Oh, how shortly we neglect:
The distinction of ideological alignment between the Home, Senate and Intelligence Department is crystal clear when seen by way of the prism of cooperation. You possibly can see which legislative committee holds the ability and help of the Intelligence Department. The Senate Intel Committee facilitates the corrupt existence of the IC Department, so the IC Department solely cooperates with the Senate Intel Committee. It truly is that easy.
• The Intelligence Department fastidiously selects its personal members by controlling how safety clearances are investigated and allowed (FBI). The Intelligence Department additionally makes use of compartmentalization of intelligence as a technique to maintain every company, and every downstream department of presidency (government, legislative and judicial), at arm’s size as a way to cease anybody from seeing the bigger image of their exercise. I name this the “silo impact“, and it’s achieved by design.
I’ve checked out shocked faces once I introduced declassified silo product from one company to the silo prospects of one other. You’ll be astonished at what they don’t know as a result of it isn’t of their ‘silo’.
 By means of the recommendation and consent guidelines, the Intelligence Department makes use of the SSCI to maintain out individuals they take into account harmful to their ongoing operations. Any appointee to the intelligence group should first move by way of the Senate Choose Committee on Intelligence, earlier than they get a full Senate vote. If the SSCI rejects the candidate, they merely refuse to take up the nomination. The president is then blocked from that appointment. That is what occurred with President Trump time and again.
By means of the recommendation and consent guidelines, the Intelligence Department makes use of the SSCI to maintain out individuals they take into account harmful to their ongoing operations. Any appointee to the intelligence group should first move by way of the Senate Choose Committee on Intelligence, earlier than they get a full Senate vote. If the SSCI rejects the candidate, they merely refuse to take up the nomination. The president is then blocked from that appointment. That is what occurred with President Trump time and again.
• Moreover, the Intelligence Department protects itself, and its facilitating allies by way of the formal classification course of. The Intelligence Department will get to resolve unilaterally what data might be launched and what data might be stored secret. There isn’t a entity outdoors the Intelligence Department, and sure that features the President of the USA, who can supersede the classification authority of the Intelligence Department. {Go Deep} and {Go Deep} That is one thing 99.9% of the individuals on our aspect get completely and frustratingly improper.
Nobody can declassify, or make public, something the Intelligence Department is not going to comply with. Doubt this? Ask Ric Grenell, John Ratcliffe, and even President Trump himself.
• The classification course of is decided contained in the Intelligence Department, all by themselves. They get to decide on what rank of classification exists on any work product they create; they usually get to resolve what the classification standing is of any work product that’s created by anybody else. The Intelligence Department has full management over what is taken into account labeled data and what’s not. The Intelligence Department defines what’s a “nationwide safety curiosity” and what’s not. An awesome method for hiding fingerprints of corrupt and criminal activity.
[For familiar reference see the redactions to Lisa Page and Peter Strzok text messages. The Intelligence Branch does all redactions.]
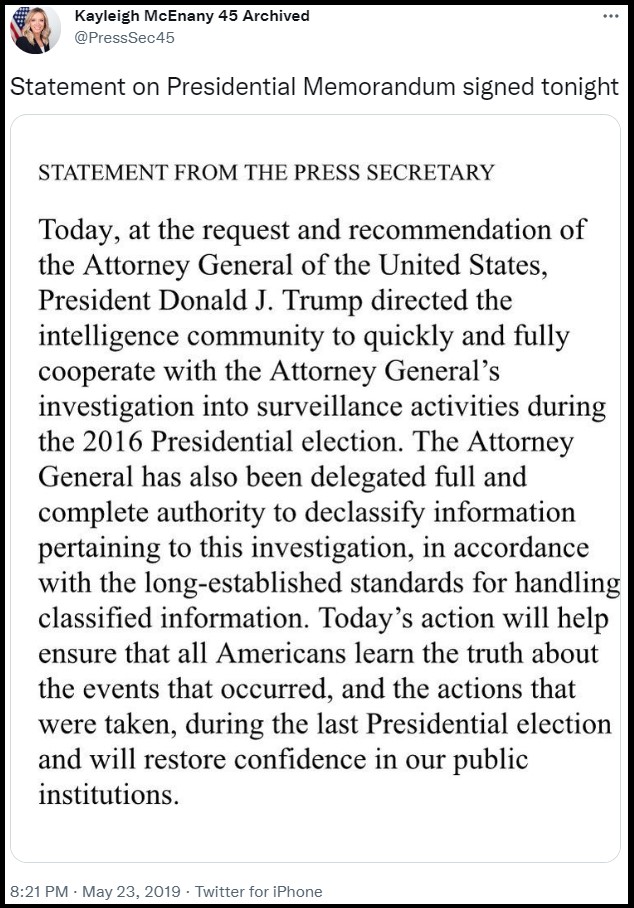 • Equally, the declassification course of is a request by an company, even a historically superior company just like the President of the USA, to the Intelligence Department asking for them to launch the knowledge. The Intelligence Department once more holds full unilateral management.
• Equally, the declassification course of is a request by an company, even a historically superior company just like the President of the USA, to the Intelligence Department asking for them to launch the knowledge. The Intelligence Department once more holds full unilateral management.
If the pinnacle of the CIA refuses to adjust to the declassification instruction of the President, what can the president do besides hearth him/her? {Once more, GO DEEP} How does the President change the non-compliant cupboard member? They should undergo the SSCI affirmation. See the issue?
Sure, there are methods to interrupt up the Intelligence Department, however they don’t begin with any congressional effort. As you’ll be able to see above, the method is the flaw – not the answer. Most conservative pundits have their emphasis on the improper syllable. Their cornerstone is fake.
For their very own self-preservation, the Intelligence Department has been interfering in our elections for years. The best way to tear this aside begins with STATE LEVEL election reform that blocks the Legislative Department from coordinating with the Intelligence Department.
The intense federalism method is vital and likewise explains why Joe Biden has instructed Legal professional Basic Merrick Garland to make use of the complete energy of the DOJ to cease state degree election reform efforts. The concern of profitable state degree election management can be why the Intelligence Department now must help the federal takeover of elections.
Our elections have been usurped by the Intelligence Department. Begin with trustworthy elections and we are going to see simply how a lot Democrat AND Republican corruption relies on manipulated election outcomes. Begin on the state degree. Begin there…. the whole lot else is downstream.
♦ COLLAPSED OVERSIGHT – The trendy system to ‘examine’ the Government Department was the creation of the legislative “Gang of Eight,” a legislative oversight mechanism supposed to supply a bridge of oversight between the authority of the intelligence group inside the Government Department.
The Go8 assemble was designed to permit the President authority to hold out intelligence operations and supply essentially the most delicate notifications to a choose group inside Congress.
The Go8 oversight is directed to the place, not the particular person, and consists of: (1) The Speaker of the Home; (2) The Minority Chief of the Home; (3) The Chair of the Home Everlasting Choose Committee on Intelligence, HPSCI; (4) The Rating Member (minority) of the HPSCI; (5) The Chief of the Senate; (6) The Minority Chief of the Senate; (7) The Chair of the Senate Choose Committee on Intelligence, SSCI; and at last (8) the Vice-Chair of the SSCI.
Instance: When the Chief Government (the President) initiates an intelligence operation on behalf of the USA, the President triggers a “discovering memo.” In essence, the instruction to the intel company or companies to authorize a covert operation. When that course of takes place, the Go8 are the primary individuals notified. Relying on the sensitivity of the operation, typically the G08 are notified instantly after the operation is carried out. The notification generally is a telephone name or an in-person briefing.
Due to the sensitivity of their intelligence data, the Gang of Eight maintain safety clearances that allow them to obtain and overview all intelligence operations. The intelligence group are additionally liable for briefing the Go8 with the identical data they use to temporary the President.

~ 2021 Gang of Eight ~
The Go8 design is meant to place intelligence oversight upon each political events in Congress; it’s designed that method by informing the minority leaders of each the Home and Senate in addition to the rating minority members of the SSCI and HPSCI. Underneath the idea, the President can not conduct an intelligence operation; and the intelligence group can not perform intelligence gathering operations with out the bulk and minority events understanding about it.
The trendy design of this oversight system was achieved to maintain rogue and/or corrupt intelligence operations from occurring. Nonetheless, as we shared within the preview to this whole dialogue, the method was usurped in the course of the Obama period. {GO DEEP}
Former FBI Director James Comey brazenly admitted to Congress on March 20, 2017, that the FBI, FBI Counterintelligence Division, DOJ and DOJ-Nationwide Safety Division, along with the Workplace of the Director of Nationwide Intelligence (ODNI) and the CIA, had been conducting impartial investigations of Donald Trump for over a yr with out informing the Go8. Comey justified the shortage of informing Go8 oversight by saying, “due to the sensitivity of the matter.”
Stupidly, Congress by no means pressed James Comey on that difficulty. The conceitedness was astounding, and the acceptance by Congress was infuriating. Nonetheless, that particular instance highlighted simply how politically corrupt the system had develop into. In essence, Crew Obama usurped your complete design of congressional oversight…. and Congress simply brushed it off.
Take note, Comey didn’t say the White Home was unaware; in truth he stated precisely the other, he stated, “The White Home was knowledgeable by way of the Nationwide Safety Council,” (the NSC). The unavoidable implication and James Comey admission that everybody simply brushed apart, was that President Obama’s Nationwide Safety Advisor, Susan Rice, was knowledgeable of the intelligence operation(s) towards Donald Trump. In spite of everything, the NSC reviews to the Nationwide Safety Advisor.
Does the January 20, 2017, Susan Rice memo look totally different now?
Once more, nobody noticed the speedy difficulty. What Comey simply described on that March Day in 2017 was the usurpation of your complete cause the Gang of Eight exists; to remove the potential for political weaponization of the Intelligence Group by the manager department. The G08 notifications to the bulk and minority are particularly designed to verify what James Comey admitted to doing was by no means presupposed to occur.
Crew Obama carried out a political operation utilizing the intelligence group and the checks-and-balances within the system had been deliberately usurped. That is an undeniable fact.
Worse nonetheless, your complete legislative department of Congress, which then particularly included the Republicans that now managed the Home and Senate, did nothing. They simply ignored what was admitted. The usurpation was willfully ignored.
The mechanism of the G08 was bypassed and not using a twitch of condemnation or investigation…. as a result of the widespread enemy was Donald Trump.
This instance highlights the collapse of the system. Obama, the Government Department, collapsed the system by usurping the method; in essence the method turned the larger difficulty, and the shortage of speedy Legislative Department response turned proof of open acceptance. The outcomes of the usurpation performed out over the subsequent 4 years, Donald J. Trump was kneecapped and misplaced his presidency due to it. Nonetheless, the larger difficulty of the collapse nonetheless exists.
The downstream consequence of the Legislative Department accepting the Government Department usurpation meant each intelligence committees had been compromised. Moreover, the management of each the Home and Senate had been complicit. Take into consideration this fastidiously. The Legislative Department allowance of the intelligence usurpation meant the Legislative Department was now subservient to the Intelligence Department.
That’s the place we’re.
Proper now.
That’s the place we’re.
Time period-3 Obama is now again within the White Home with Joe Biden.
NOTE: Former Obama Nationwide Safety aide and counsel to the President, Lisa Monaco, is in her present place as Deputy Legal professional Basic, particularly to verify all of those revelations don’t develop into a authorized danger to Barack Obama and the individuals who created them. The SSCI confirmed Monaco for this goal as a result of the Senate is simply as a lot in danger.
Time period-1 and Time period-2 Obama usurped the ‘examine and stability‘ inside the system and weaponized the intelligence equipment. Throughout Trump’s time period that weaponization was coated up by a compliant congress, complicit senate intelligence committee, and never a single member of the oversight known as it out. Now, Time period-3 Obama steps again in to proceed the duvet up and proceed the weaponization.
Hopefully, now you can see the dimensions of the issue that surrounds us with particular quotation for what has taken place. What I simply defined to you above isn’t conspiracy idea, it’s admitted incontrovertible fact that anybody can look upon. But….
Have you ever seen this talked about anyplace? Have you ever seen this known as out by anybody in Congress? Have you ever seen anybody in media (ally or adversary) name this out? Have you ever seen any member of the Judicial Department arise and say wait, what’s happening isn’t okay? Have you ever seen a single candidate for elected workplace level this out? Have you ever seen anybody advising a candidate to level this out?
That is our present standing. It isn’t deniable. The reality exists no matter our consolation.
Not a single particular person in energy will say brazenly what has taken place. They’re afraid of the Fourth Department. The proof of what has taken place is true there in entrance of our face. The phrases, actions and actions of those that participated on this course of will not be deniable, in truth most of it’s on report.
There are solely two members of the Gang of Eight who’ve existed in place from January 2007 (the true starting of Obama’s time period, two years earlier than he took workplace when the Congress flipped). Solely two members of the G08 have been persistently in place from January of 2007 to proper now, in the present day. All of the others got here and went, however two members of the Gang of Eight have been a part of that failed and collapsed oversight all through the previous 15 years, Nancy Pelosi and Mitch McConnell.
 ♦ TECHNOLOGY – On a worldwide scale – the fashionable intelligence gathering networks are actually depending on knowledge assortment to execute their intelligence missions. Within the digital age nations have been executing numerous strategies to collect that knowledge. Digital surveillance has changed different strategies of interception. These surveillance efforts have resulted in a coalescing of regional knowledge networks primarily based on historic multi-national relationships.
♦ TECHNOLOGY – On a worldwide scale – the fashionable intelligence gathering networks are actually depending on knowledge assortment to execute their intelligence missions. Within the digital age nations have been executing numerous strategies to collect that knowledge. Digital surveillance has changed different strategies of interception. These surveillance efforts have resulted in a coalescing of regional knowledge networks primarily based on historic multi-national relationships.
We’ve a latest body of reference for the “U.S. knowledge assortment community” inside the NSA. By means of the allied course of the 5 Eyes nations all depend on the NSA surveillance database (U.Ok, Australia, Canada, New Zealand and U.S.) The NSA database offers the digital baseline for intelligence operations in protection of our allies. The portals into the NSA database are basically an meeting of allies in like-minded ideological connection to the USA.
Sadly, there have been some revelations concerning the NSA database getting used to observe our allies, like within the instance of Germany and surveillance on Angela Merkel’s telephone. So long as “the great guys” are working honorably, allies of the USA can really feel assured about having safety from the NSA surveillance of worldwide digital knowledge. We warn our mates if we detect one thing harmful and so on.
The U.S. has nodes on communication pipelines to intercept and extract knowledge. We’ve additionally launched a whole bunch, maybe 1000’s, of satellites to conduct surveillance and collect up knowledge. All of this knowledge is fed into the NSA database the place it’s monitored (presumably) as a nationwide safety mechanism, and in protection of our allies.
Nonetheless, what about knowledge assortment or knowledge networks which can be outdoors the NSA database? What do our enemies do? The NSA database is only one intelligence operation of digital surveillance amid your complete world, and we don’t enable entry by adversaries we’re monitoring. So what do they do? What do our allies do who may not belief the USA resulting from previous inconsistencies, ie. the Center East?
The solutions to these questions spotlight different knowledge assortment networks. So, a quick overview of the foremost gamers is required.
♦ CHINA – China operates their very own database. They, just like the NSA, scoop up knowledge for his or her system. Like us, China launches satellites and deploys different digital knowledge assortment strategies to obtain into their database. Because of this the problems of digital gadgets manufactured in China turns into problematic. A part of the Chinese language knowledge assortment system includes using spyware and adware, hacking and extraction.
Points with Chinese language communication firm Huawei tackle an added dimension when you think about the objective of the Chinese language authorities to conduct surveillance and assemble a community of knowledge to compete with the USA by way of the NSA. Different Chinese language strategies of surveillance and data-collection are much less subversive, as within the examples of TicTok and WeChat. These are Chinese language social media firms which can be scraping knowledge similar to the NSA scrapes knowledge from Fb, Twitter and different Silicon Valley tech firms. [ Remember, the Intelligence Branch is a public-private partnership. ]
♦ RUSSIA – It is extremely probably that Russia operates their very own database. We all know Russia launches satellites, similar to China and the USA, for a similar functions. Russia can be very proficient at hacking into different databases and extracting data to retailer and make the most of in their very own community. The distinction between the U.S., China and Russia is probably going that Russia spends extra time on the hacking facet as a result of they don’t generate precise know-how techniques as quickly because the U.S. and China.
The latest database creation is an end result of an ally having to take motion as a result of they can not depend on the ideology of the USA remaining constant, because the administrations ping-pong primarily based on ideology.
♦ SAUDI ARABIA – Sure, in 2016 we found that Saudi Arabia was now working their very own intelligence data-gathering operation. It might make sense, given the character of the Center East and the fixed fluctuations in political help from the USA. It’s a lesson the allied Arab group and Gulf Cooperation Council discovered shortly when President Obama went to Cairo in 2009 and launched the Islamist Spring (Arab Spring) upon them.


I’ve little doubt the creation of the Saudi intelligence community was particularly as a result of the Obama administration began supporting radical Islamists inside the Muslim Brotherhood and threw gas on the fires of extremism everywhere in the Arab world.
Give it some thought., What would you do for those who had been Saudi Arabia, Egypt, Bahrain, Kuwait, the UAE, Jordan, Oman or Yemen and also you knew the USA may simply set off an inside rebellion of al-Qaeda, ISIS and the political arm of the Muslim Brotherhood to hunt your destruction?
Undoubtedly, these pressing classes from 2009, 2010, 2011 triggered the formation of the Arab Intelligence Community as a community to defend itself with consistency. They assembled the community and activated it in 2017 as pictured above.
♦ Israel – Alongside the same outlook to the Arab community, little doubt Israel operates an impartial knowledge assortment system as a way of defending itself from ever-changing U.S. politics amid a area that’s extraordinarily hostile to its very existence. Just like the others, Israel launches proprietary satellites, and we could be certain they use covert strategies to collect digital knowledge similar to the U.S. and China.
As we’ve got not too long ago seen within the Pegasus story, Israel creates spyware and adware applications which can be in a position to observe and monitor cellphone communications of targets. The spyware and adware wouldn’t work until Israel had entry to some community the place the telephone meta-data was truly saved. So yeah, it is sensible for Israel to function an impartial intelligence database.
♦ Abstract: As we perceive the USA Intelligence Department of presidency because the superseding entity that controls the inner politics of our nation, we additionally should take into account that a number of nations have the identical difficulty. There are main intelligence networks around the globe beside the NSA “5-Eyes” database. China, Russia, Saudi Arabia and Israel all function proprietary databases deploying the identical instruments and strategies for meeting.
The geopolitical battle that has at all times existed has now shifted right into a digital battle-space. The Intelligence Companies from these areas are actually working because the spine of the federal government that makes use of them and has develop into depending on them. [<- Reread that].
When you settle for the digital-era intelligence equipment of China, Russia, Saudi-Arabia, The USA and Israel, are actually the first nationwide safety mechanisms for stabilization of presidency; you then settle for the significance of these intelligence operations.
When you perceive how foundational these trendy intelligence operations have develop into for the steadiness and continuity of these governments…… you then start to grasp simply how the USA intelligence group turned extra necessary than the federal government that created it.
From that time it’s then vital to grasp that home intelligence operations are underway to observe the digital communication of Americans inside our personal nation. YOU are beneath surveillance. The dad and mom who confront college boards are beneath surveillance. The political operatives contained in the FBI are monitoring everybody who comes onto the radar, that’s the reason the Nationwide Faculty Boards Affiliation requested the White Home, then the DOJ, to have the FBI begin concentrating on dad and mom. Are issues making sense now?
♦ Public Personal Partnership – The trendy Fourth Department of Authorities is just doable due to a Public-Personal partnership with the intelligence equipment. You would not have to take my phrase for it, the partnership is so brazened they’ve made public admissions.
 The largest names in Large Tech introduced in June their partnership with the 5 Eyes intelligence community, in the end managed by the NSA, to: (1) monitor all exercise of their platforms; (2) determine extremist content material; (3) search for expressions of Home Violent Extremism (DVE); after which, (4) put the content material particulars right into a database the place the 5 Eyes intelligence companies (U.Ok., U.S., Australia, Canada, New Zealand) can entry it.
The largest names in Large Tech introduced in June their partnership with the 5 Eyes intelligence community, in the end managed by the NSA, to: (1) monitor all exercise of their platforms; (2) determine extremist content material; (3) search for expressions of Home Violent Extremism (DVE); after which, (4) put the content material particulars right into a database the place the 5 Eyes intelligence companies (U.Ok., U.S., Australia, Canada, New Zealand) can entry it.
Fb, Twitter, Google and Microsoft are all partnering with the intelligence equipment. It is perhaps troublesome to fathom how brazenly they admit this, however they do. Take a look at this sentence in the press launch (emphasis mine):
[…] “The Group will use lists from intelligence-sharing group 5 Eyes including URLs and PDFs from extra teams, together with the Proud Boys, the Three Percenters and neo-Nazis.”
Take into consideration that sentence construction very fastidiously. They’re “including to” the preexisting listing…. admitting the group (aka Large Tech) have already got entry to the the intelligence-sharing database… and likewise admitting there’s a preexisting listing created by the 5 Eyes consortium.
Clearly, who and what’s outlined as “extremist content material” might be decided by the Large Tech insiders themselves. This offers a gateway, one other believable deniability facet, to cowl the Intelligence Department from any oversight.
When the Intelligence Department inside authorities needs to conduct surveillance and monitor Americans, they run up towards issues as a result of Structure of the USA. They get round these authorized limitations by sub-contracting the intelligence gathering, the precise knowledge mining, and permitting outdoors events (contractors) to have entry to the central database.
The federal government can not conduct digital searches (4th modification difficulty) and not using a warrant; nevertheless, personal people can search and report again so long as they’ve entry. What’s being admitted is strictly that preexisting partnership. The distinction is that Large Tech will flag the content material from inside their platforms, and now a secondary database stuffed with the extracted data might be offered brazenly for the Intelligence Department to take advantage of.
 The quantity of metadata captured by the NSA has at all times been an issue due to the filters wanted to make the concentrating on helpful. There’s a number of noise in amassing all knowledge that makes the elements you actually wish to determine harder to seize. This new admission places a brand new huge filtration system within the metadata that circumvents any privateness protections for people.
The quantity of metadata captured by the NSA has at all times been an issue due to the filters wanted to make the concentrating on helpful. There’s a number of noise in amassing all knowledge that makes the elements you actually wish to determine harder to seize. This new admission places a brand new huge filtration system within the metadata that circumvents any privateness protections for people.
Beforehand, the Intelligence Department labored across the constitutional and illegal search difficulty through the use of sources that weren’t in the USA. A home U.S. company, engaged on behalf of the U.S. authorities, can not pay attention in your calls and not using a warrant. Nonetheless, if the U.S. company sub-contracts to say a Canadian group, or international ally, the privateness invasion is not legally restricted by U.S. regulation.
What was introduced in June 2021 is an alarming admission of a previous relationship together with open intent to outline their home political opposition as extremists.
July 26 (Reuters) – A counterterrorism group shaped by a number of the largest U.S. tech firms together with Fb (FB.O) and Microsoft (MSFT.O) is considerably increasing the forms of extremist content material shared between companies in a key database, aiming to crack down on materials from white supremacists and far-right militias, the group advised Reuters.
Till now, the World Web Discussion board to Counter Terrorism’s (GIFCT) database has targeted on movies and pictures from terrorist teams on a United Nations listing and so has largely consisted of content material from Islamist extremist organizations akin to Islamic State, al Qaeda and the Taliban.
Over the subsequent few months, the group will add attacker manifestos – usually shared by sympathizers after white supremacist violence – and different publications and hyperlinks flagged by U.N. initiative Tech In opposition to Terrorism. It’s going to use lists from intelligence-sharing group 5 Eyes, including URLs and PDFs from extra teams, together with the Proud Boys, the Three Percenters and neo-Nazis.
The companies, which embrace Twitter (TWTR.N) and Alphabet Inc’s (GOOGL.O) YouTube, share “hashes,” distinctive numerical representations of unique items of content material which have been faraway from their providers. Different platforms use these to determine the identical content material on their very own websites to be able to overview or take away it. (learn extra)
The affect of the Intelligence Department now reaches into our lives, our private lives.
[The Intercept] – […] Behind closed doorways, and thru strain on personal platforms, the U.S. authorities has used its energy to attempt to form on-line discourse. In accordance with assembly minutes and different data appended to a lawsuit filed by Missouri Legal professional Basic Eric Schmitt, a Republican who can be working for Senate, discussions have ranged from the dimensions and scope of presidency intervention in on-line discourse to the mechanics of streamlining takedown requests for false or deliberately deceptive data.
“Platforms have gotten to get snug with gov’t. It’s actually attention-grabbing how hesitant they continue to be,” Microsoft government Matt Masterson, a former DHS official, texted Jen Easterly, a DHS director, in February.
In a March assembly, Laura Dehmlow, an FBI official, warned that the specter of subversive data on social media may undermine help for the U.S. authorities. Dehmlow, in response to notes of the dialogue attended by senior executives from Twitter and JPMorgan Chase, careworn that “we’d like a media infrastructure that’s held accountable.” (learn extra)
Within the a long time earlier than 9/11/01 the intelligence equipment intersected with authorities, influenced authorities, and undoubtedly managed many establishments with it. The legislative oversight operate was weak and rising weaker, however it nonetheless existed and will have been used to maintain the IC in examine. Nonetheless, after the occasions of 9/11/01, the short-sighted legislative reactions opened the door to permit the surveillance state to weaponize towards home enemies.
[…] The extent to which the DHS initiatives have an effect on People’ day by day social feeds is unclear. Throughout the 2020 election, the federal government flagged quite a few posts as suspicious, a lot of which had been then taken down, paperwork cited within the Missouri lawyer common’s lawsuit disclosed. And a 2021 report by the Election Integrity Partnership at Stanford College discovered that of practically 4,800 flagged gadgets, know-how platforms took motion on 35 p.c — both eradicating, labeling, or soft-blocking speech, which means the customers had been solely in a position to view content material after bypassing a warning display screen. The analysis was achieved “in session with CISA,” the Cybersecurity and Infrastructure Safety Company.
Previous to the 2020 election, tech firms together with Twitter, Fb, Reddit, Discord, Wikipedia, Microsoft, LinkedIn, and Verizon Media met on a month-to-month foundation with the FBI, CISA, and different authorities representatives. In accordance with NBC Information, the conferences had been a part of an initiative, nonetheless ongoing, between the personal sector and authorities to debate how companies would deal with misinformation in the course of the election. (maintain studying)
After the Patriot Act was triggered, not coincidentally solely six weeks after 9/11, a sluggish and harmful fuse was lit that ends with the intelligence equipment being granted a large quantity of energy. Concurrently the mission of the intelligence group now encompassed monitoring home threats as outlined by the individuals who function the surveillance system.
The issue with assembled energy is at all times what occurs when a Machiavellian community takes management over that energy and begins the method to weaponize the instruments for their very own malicious profit. That’s precisely what the community of President Barack Obama did.
The Obama community took pre-assembled intelligence weapons (we must always by no means have allowed to be created) and turned these FBI, DOJ-NSD, DHS and ODNI weapons into political instruments for his radical and elementary change. The goal was the important material of our nation.
Finally, this corrupt political course of gave energy to create the Fourth Department of Authorities, the Intelligence Department and a large nationwide surveillance state. From that perspective the elemental change was profitable.
That is the dimensions of corrupt political compromise on each side of the DC dynamic that we’re up towards. Preserving this surveillance system, a public-private partnership, can be what eradicating Donald Trump was all about…. The concentrating on of President Trump to be able to protect the system, the system that was weaponized in the course of the Obama administration, is what the actions of the DOJ, FBI and DHS are all about.
What would highly effective individuals in DC do to cease the American individuals from discovering this out?
A managed 2020 election? An elevated censorship within the aftermath? A raid on Mar-a-Lago?
…The necessity for management is a response to worry.